Add a Calculated Field Legal Utah Identity Theft Forms For Free
How it works
-

Import your Utah Identity Theft Forms from your device or the cloud, or use other available upload options.
-
Make all necessary changes in your paperwork — add text, checks or cross marks, images, drawings, and more.
-

Sign your Utah Identity Theft Forms with a legally-binding electronic signature within clicks.
-
Download your completed work, export it to the cloud, print it out, or share it with others using any available methods.
How to Add a Calculated Field Legal Utah Identity Theft Forms For Free
Are you tired of endless document printing, scanning, postal delivery, and spending precious time and resources with manual fill-out? The times have moved on, and the easiest way to Add a Calculated Field Legal Utah Identity Theft Forms For Free and make any other critical updates to your forms is by handling them online. Choose our quick and reliable online editor to fill out, edit, and execute your legal documentation with highest effectiveness.
Here are the steps you should take to Add a Calculated Field Legal Utah Identity Theft Forms For Free quickly and effortlessly:
- Upload or import a file to the service. Drag and drop the template to the upload area, import it from the cloud, or use another option (extensive PDF catalog, emails, URLs, or direct form requests).
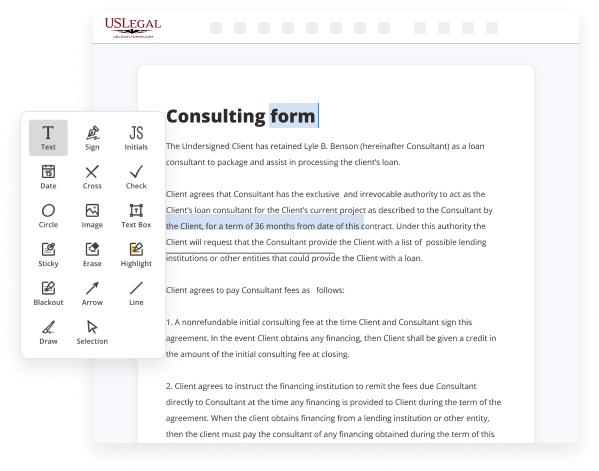
- Provide the required information. Fill out empty fields utilizing the Text, Check, and Cross tools from our top pane. Use our editor’s navigation to make certain you’ve filled in everything. Point out the most important details with the Highlight option and erase or blackout areas with no value.
- Adjust and rearrange the form. Use our upper and side toolbars to change your content, place additional fillable fields for different data types, re-order pages, add new ones, or remove unnecessary ones.
- Sign and request signatures. Whatever method you choose, your eSignature will be legally binding and court-admissible. Send your form to other people for approval through email or signing links. Notarize the paperwork right in our editor if it needs witnessing.
- Share and save the copy. Download or export your accomplished documentation to the cloud in the format you need, print it out if you require a hard copy, and select the most suitable file-sharing option (email, fax, SMS, or sent by snail mail using the USPS).
With our service, you don’t have any more excuses to accomplish legal documents manually. Save time and effort executing them online twice as fast and more efficiently. Give it a try now!

Benefits of Editing Utah Identity Theft Forms Online
Top Questions and Answers
Form 14039 can also be completed online at .
Video Guide to Add a Calculated Field Legal Utah Identity Theft Forms For Free
Penal Code 5-3 0.5 is California's primary law addressing criminal identity theft and identity theft is defined as using another person's identifying information in order to harm that person or to obtain an unjust benefit for yourself so this information could include the person's name date of birth address social security number driver's license number bank account or credit card
Number or passwords now it's illegal to use this information it's also illegal to collect this information to possess this information or to sell this information if you do so with a fraudulent intent now the typical examples where we see prosecution is when somebody uses another person's credit card to make purchases online or applies for mortgage using another

Tips to Add a Calculated Field Legal Utah Identity Theft Forms For Free
- Understand the purpose of the calculated field and what data you want to include.
- Familiarize yourself with the software or platform you are using for the forms.
- Locate the section within the form editor where you can add a calculated field.
- Determine the formula you need to use for your calculations.
- Use correct syntax to avoid errors in your calculated field.
- Test the calculated field to ensure it is working as expected.
- Document any changes you make for future reference.
You might need to use this editing feature when there are changes in identity theft laws or when you need to customize the forms for specific cases.
Related Searches
Utah's ID Theft Central Site – Tools for reporting ID theft and repairing after a theft occurs, plus resources for protecting children. This affidavit is for victims of identity theft. To avoid delays do not use this form if you have already filed a Form 14039 for this incident. The IRS wants you to submit Form 14039 when you believe someone has unauthorized access to your personal information. IdentityTheft.gov is the federal government's one-stop resource for identity theft victims. The site provides streamlined checklists and sample letters. Recovering from identity theft is a process. Here's step-by-step advice that can help you limit the damage, report identity theft, and fix your credit. Identity theft insurance can help you recover from the costs related to identity theft, including legal fees and lost wages. We're pleased to roll out our new TTB Processing Times for Tax Claims and Refunds.
Industry-leading security and compliance
-
In businnes since 1997Over 25 years providing professional legal documents.
-
Accredited businessGuarantees that a business meets BBB accreditation standards in the US and Canada.
-
Secured by BraintreeValidated Level 1 PCI DSS compliant payment gateway that accepts most major credit and debit card brands from across the globe.
-
VeriSign secured#1 Internet-trusted security seal. Ensures that a website is free of malware attacks.