Extract Data From Legal Pennsylvania Computers Forms For Free
How it works
-

Import your Pennsylvania Computers Forms from your device or the cloud, or use other available upload options.
-
Make all necessary changes in your paperwork — add text, checks or cross marks, images, drawings, and more.
-

Sign your Pennsylvania Computers Forms with a legally-binding electronic signature within clicks.
-
Download your completed work, export it to the cloud, print it out, or share it with others using any available methods.
How to Extract Data From Legal Pennsylvania Computers Forms For Free
Are you tired of endless document printing, scanning, postal delivery, and wasting precious time and resources with manual fill-out? The times have moved on, and the best way to Extract Data From Legal Pennsylvania Computers Forms For Free and make any other essential updates to your forms is by handling them online. Take advantage of our quick and reliable online editor to complete, edit, and execute your legal documentation with highest efficiency.
Here are the steps you should take to Extract Data From Legal Pennsylvania Computers Forms For Free quickly and effortlessly:
- Upload or import a file to the service. Drag and drop the template to the upload area, import it from the cloud, or use another option (extensive PDF library, emails, URLs, or direct form requests).
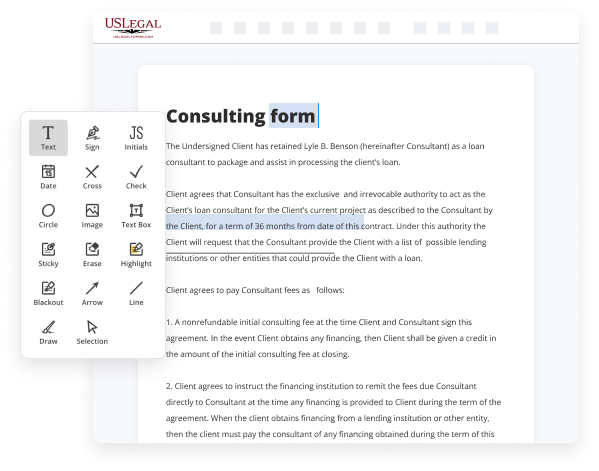
- Provide details you need. Fill out blank fields using the Text, Check, and Cross tools from our upper pane. Use our editor’s navigation to ensure you’ve filled in everything. Point out the most important details with the Highlight option and erase or blackout areas with no value.
- Modify and rearrange the template. Use our upper and side toolbars to change your content, place additional fillable fields for different data types, re-order sheets, add new ones, or remove redundant ones.
- Sign and request signatures. Whatever method you select, your eSignature will be legally binding and court-admissible. Send your form to others for signing through email or signing links. Notarize the paperwork right in our editor if it needs witnessing.
- Share and save the copy. Download or export your completed documentation to the cloud in the file format you need, print it out if you prefer a physical copy, and select the most suitable file-sharing option (email, fax, SMS, or delivered by snail mail using the USPS).
With our service, you don’t have any more excuses to complete legal documents manually. Save time and effort executing them online twice as quickly and more properly. Try it out now!

Benefits of Editing Pennsylvania Computers Forms Online
Top Questions and Answers
Pennsylvania law separates invasion of privacy claims into four different causes of action ? in the state of Pennsylvania, you are protected against: Intrusion upon your seclusion; Intentional interference with your private life that would be highly offensive to an ordinary person, causing shame, humiliation, etc.
Video Guide to Extract Data From Legal Pennsylvania Computers Forms For Free
Hello everyone Emilia from bit Scout and in this video I wanted to show you a new feature that we've just deployed to our platform and it allows you to extract data practically from any document just a few examples so here how it works first we go to create plugin and we press extract in this case we're going
To extract data from file and this is the new screen that we have deployed and you will see in your bits code that allows you to first load an example okay so this is a document called the SEC filling form 8ka for Apple let's say I want to extract some information from this form which and what I

Related Features
Related Searches
Our computer forensics technology extracts and collects all files on the computer. This includes PDFs, Word files, photographs, videos, metadata, and other ... Currently, looking up some specific information is almost impossible. Our goal is to automate the processing of these cases: to categorize each ... b. Commonwealth Data. Any information, records or files, regardless of form, that are owned, managed, processed, generated or stored by the. The Legislative Data Processing Center (LDPC) is a service agency of the Pennsylvania General Assembly. Created by the act of December 10, 1968 ( P.L.1158, ... A territorial limit on searches of computer data poses problems for law enforcement because computer data stored in a computer network can be located. The law defines 'identifying information' as '[a]ny document, photographic, pictorial or computer image of another person, or any fact used to establish ... (d) Extracting from the record.--When criminal history record information is maintained by a criminal justice agency in records containing investigative ... Information to noncriminal justice agencies and individuals, it shall extract ... automatically accepting and processing data, including computer programs, data. Helping you navigate export control laws and sanctions regulations applicable to your Penn activities. Additional Information. Export Controls in Research ... By Y LELKES · Cited by 3 ? These laws, which attempt to regulate data extraction by providing consumers with rights to access the information companies have about them, rights to request ...
Industry-leading security and compliance
-
In businnes since 1997Over 25 years providing professional legal documents.
-
Accredited businessGuarantees that a business meets BBB accreditation standards in the US and Canada.
-
Secured by BraintreeValidated Level 1 PCI DSS compliant payment gateway that accepts most major credit and debit card brands from across the globe.
-
VeriSign secured#1 Internet-trusted security seal. Ensures that a website is free of malware attacks.