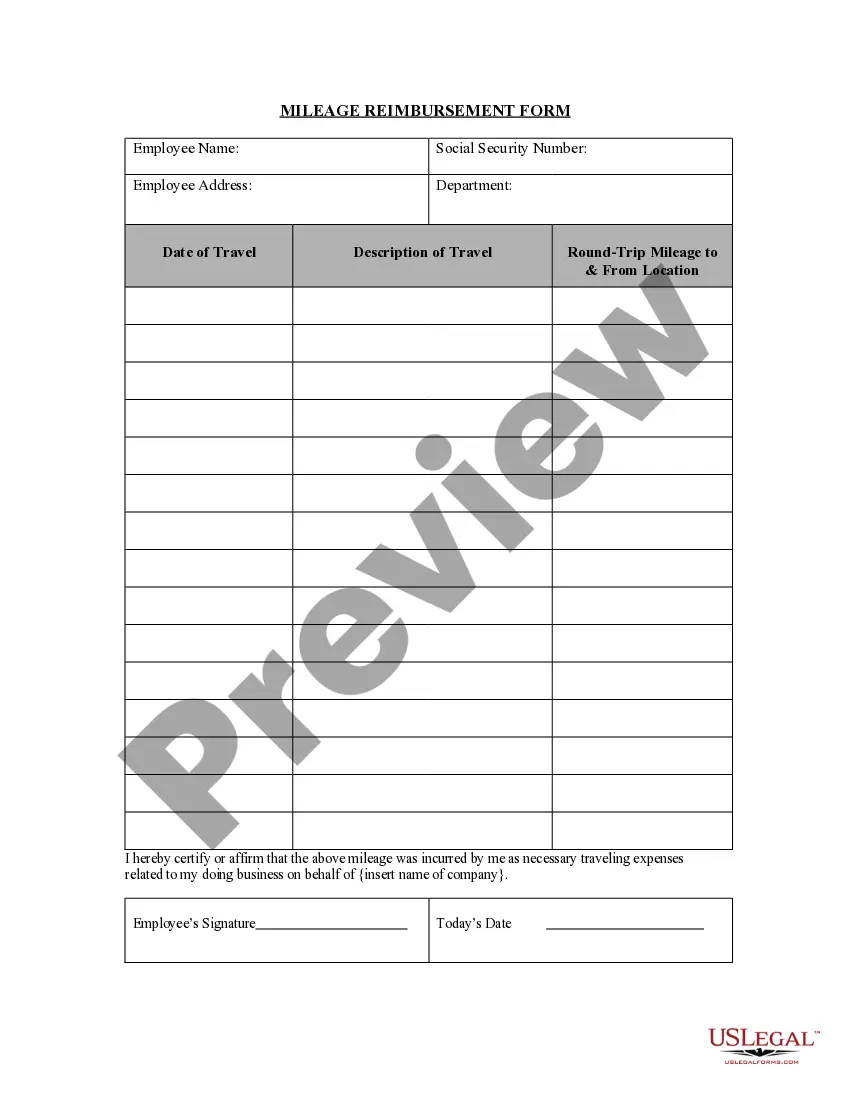
This document is an important policy for a company that relies on its information assets and computer resources to conduct and support its business operations with its customers, employees and suppliers. It seeks to protect business development information, manufacturing and operation information, software and product development, and data security.
Cook Illinois is committed to ensuring the highest level of information security for its employees and stakeholders. To achieve this, the company has implemented a comprehensive Employee Policy for Information Security that outlines the guidelines, procedures, and best practices for protecting sensitive information from unauthorized access, disclosure, loss, or theft. The Cook Illinois Employee Policy for Information Security comprises various types of policies, including: 1. Acceptable Use Policy: This policy sets out the rules and guidelines for using company-provided information systems, devices, and resources. It specifies the acceptable and prohibited activities to prevent misuse of technology assets and maintain a secure working environment. 2. Password Policy: To protect sensitive information, Cook Illinois has a robust password policy that mandates strong and unique passwords. This policy defines the requirements for password complexity, frequency of password changes, and the prohibition of password sharing. 3. Data Classification Policy: Cook Illinois recognizes that not all information is equal in terms of sensitivity and criticality. The Data Classification Policy categorizes data into different levels of sensitivity, such as public, internal, confidential, or restricted. It outlines the appropriate handling procedures for each classification, including access controls, data storage, and encryption requirements. 4. Remote Access Policy: With the increasing need for remote work arrangements, Cook Illinois has a Remote Access Policy that governs the secure access to company resources from external networks or devices. This policy outlines the requirements for secure authentication, data encryption, and protection against unauthorized access or data leakage. 5. Incident Response Policy: In the event of a security incident or data breach, Cook Illinois has an Incident Response Policy that provides a framework for timely and effective response. This policy defines roles and responsibilities during an incident, reporting procedures, and guidance for mitigating the impact of security breaches. 6. Mobile Device Policy: As mobile devices pose additional security risks, Cook Illinois has implemented a Mobile Device Policy to ensure the secure use of smartphones, tablets, and other portable devices. This policy addresses issues such as device encryption, remote wipe capabilities, and the installation of approved security applications. These various policies collectively form the Cook Illinois Employee Policy for Information Security, designed to safeguard sensitive information, protect the company's reputation, and maintain compliance with relevant laws and regulations. By adhering to these policies, employees can contribute to a secure and reliable working environment while minimizing the risk of data breaches and cyber threats.Cook Illinois is committed to ensuring the highest level of information security for its employees and stakeholders. To achieve this, the company has implemented a comprehensive Employee Policy for Information Security that outlines the guidelines, procedures, and best practices for protecting sensitive information from unauthorized access, disclosure, loss, or theft. The Cook Illinois Employee Policy for Information Security comprises various types of policies, including: 1. Acceptable Use Policy: This policy sets out the rules and guidelines for using company-provided information systems, devices, and resources. It specifies the acceptable and prohibited activities to prevent misuse of technology assets and maintain a secure working environment. 2. Password Policy: To protect sensitive information, Cook Illinois has a robust password policy that mandates strong and unique passwords. This policy defines the requirements for password complexity, frequency of password changes, and the prohibition of password sharing. 3. Data Classification Policy: Cook Illinois recognizes that not all information is equal in terms of sensitivity and criticality. The Data Classification Policy categorizes data into different levels of sensitivity, such as public, internal, confidential, or restricted. It outlines the appropriate handling procedures for each classification, including access controls, data storage, and encryption requirements. 4. Remote Access Policy: With the increasing need for remote work arrangements, Cook Illinois has a Remote Access Policy that governs the secure access to company resources from external networks or devices. This policy outlines the requirements for secure authentication, data encryption, and protection against unauthorized access or data leakage. 5. Incident Response Policy: In the event of a security incident or data breach, Cook Illinois has an Incident Response Policy that provides a framework for timely and effective response. This policy defines roles and responsibilities during an incident, reporting procedures, and guidance for mitigating the impact of security breaches. 6. Mobile Device Policy: As mobile devices pose additional security risks, Cook Illinois has implemented a Mobile Device Policy to ensure the secure use of smartphones, tablets, and other portable devices. This policy addresses issues such as device encryption, remote wipe capabilities, and the installation of approved security applications. These various policies collectively form the Cook Illinois Employee Policy for Information Security, designed to safeguard sensitive information, protect the company's reputation, and maintain compliance with relevant laws and regulations. By adhering to these policies, employees can contribute to a secure and reliable working environment while minimizing the risk of data breaches and cyber threats.
Para su conveniencia, debajo del texto en español le brindamos la versión completa de este formulario en inglés. For your convenience, the complete English version of this form is attached below the Spanish version.