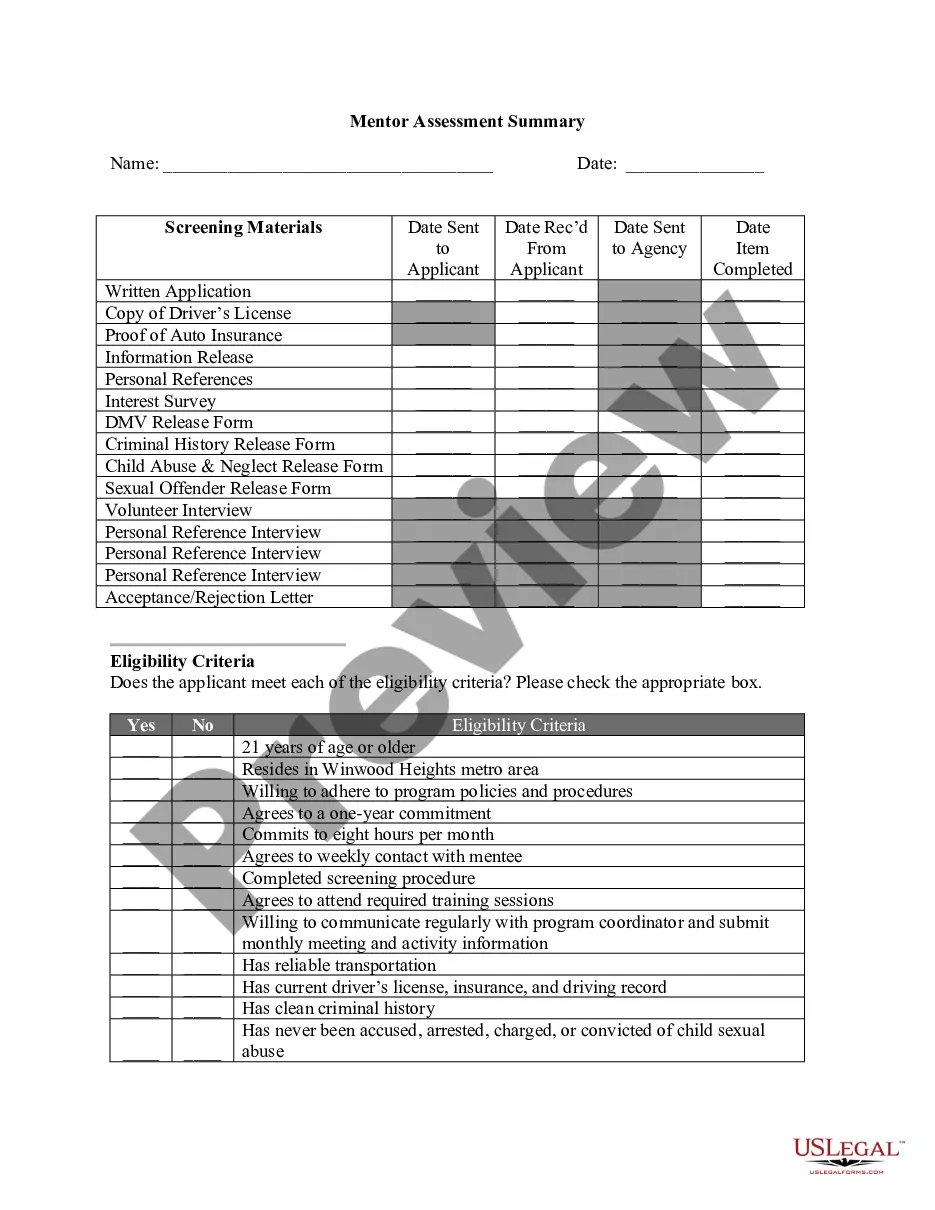
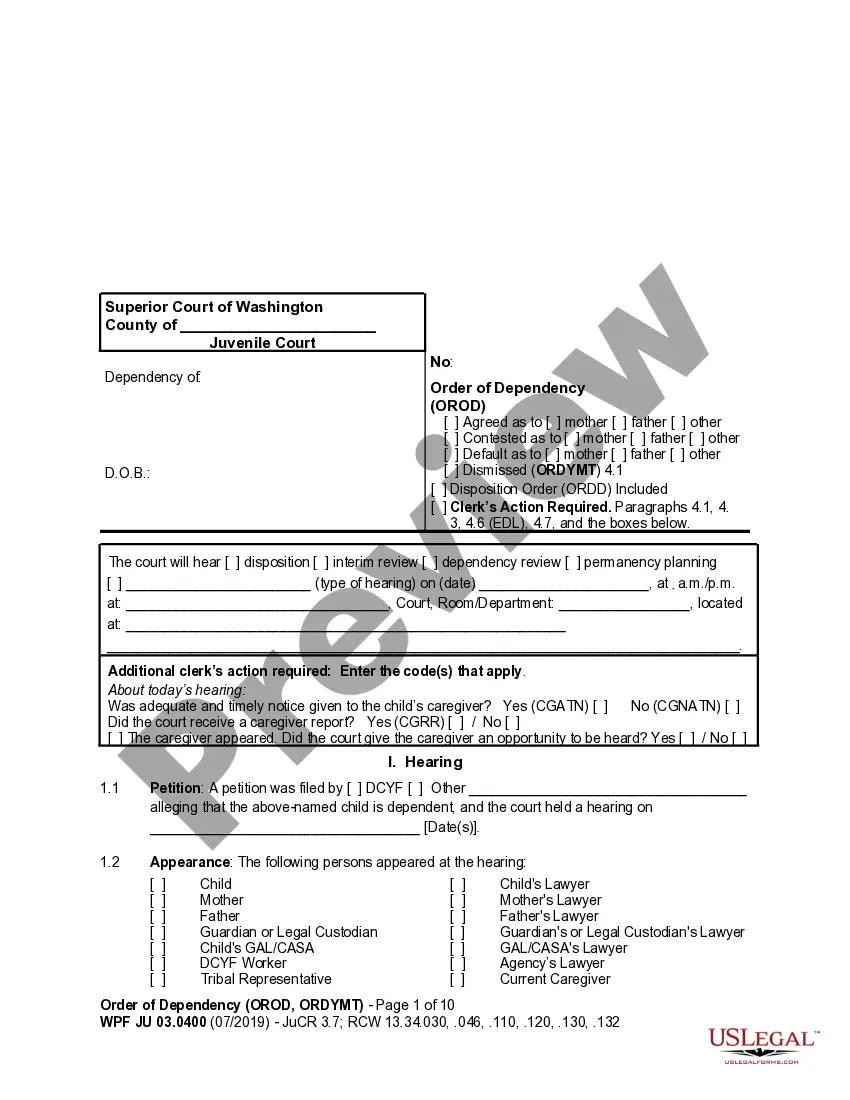
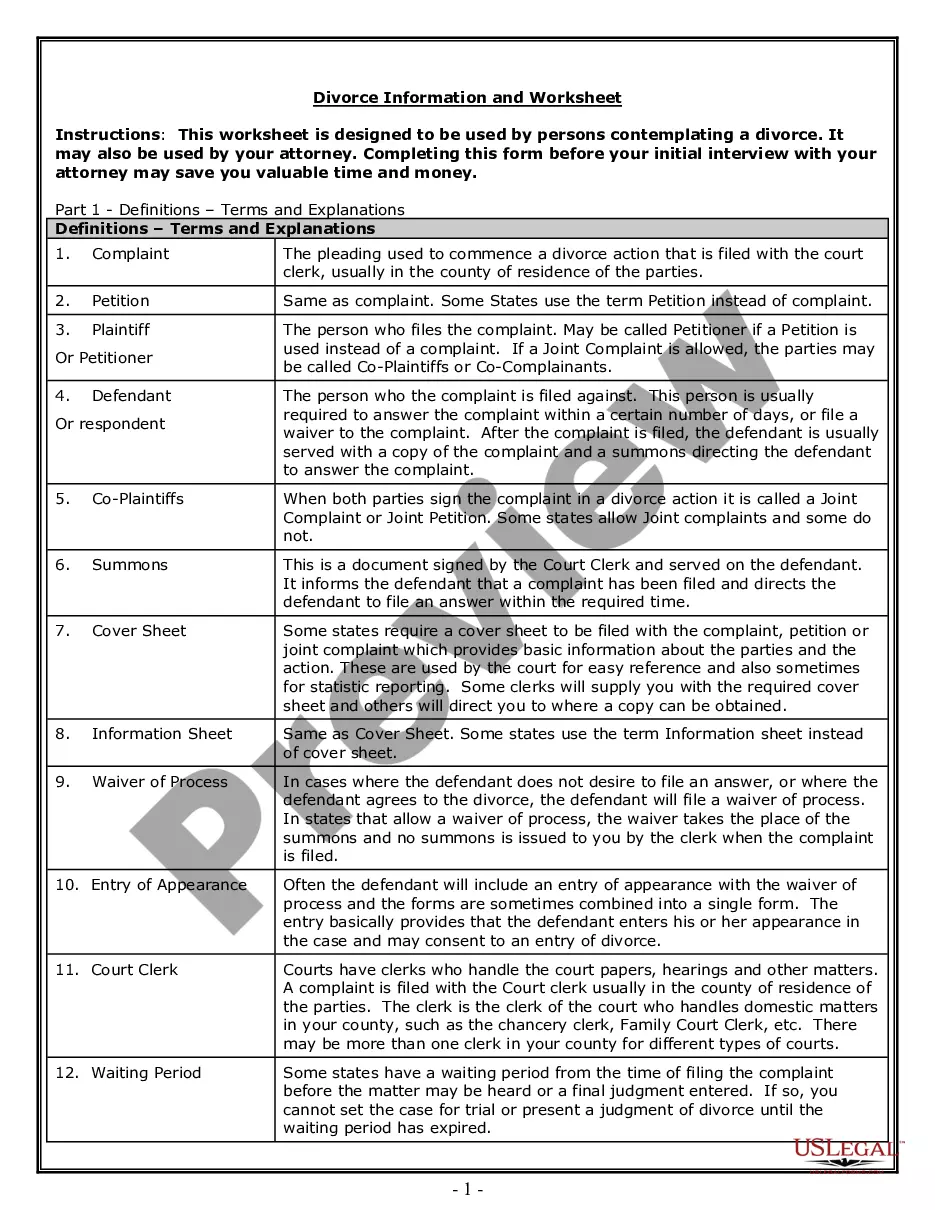
Delaware Ethical Hacking Agreement for External Network Security — Unannounced Penetration Test is a comprehensive and vital document that outlines the terms and conditions for conducting ethical hacking activities on an organization's external network. This agreement ensures that both parties involved, the organization and the ethical hacker, are aware of their responsibilities, rights, and limitations during the penetration testing process. The primary aim of the Delaware Ethical Hacking Agreement for External Network Security — Unannounced Penetration Test is to assess the robustness and vulnerabilities of an organization's external network by simulating real-world cyberattacks without prior notice. This type of penetration test aims to evaluate the effectiveness of the existing security measures and identify potential weaknesses that malicious actors could exploit. This agreement covers various aspects to provide a clear framework for the penetration testing engagement. It defines the scope of the test, including the specific systems, networks, and applications that will be targeted. It also specifies the testing techniques and tools that will be used, adhering to industry best practices and ethical guidelines. Moreover, the Delaware Ethical Hacking Agreement for External Network Security — Unannounced Penetration Test states the timeframes and schedules agreed upon for the testing process to minimize disruption to the organization's operations. It also establishes the rules of engagement, such as what actions the ethical hacker can perform and what should be avoided to prevent any damage or unauthorized access. This agreement also addresses the legal aspects, emphasizing that the ethical hacker should not engage in any illegal activities during the testing process. It ensures that all applicable laws and regulations are respected, and the ethical hacker acts within the boundaries of authorized activities. The Delaware Ethical Hacking Agreement for External Network Security — Unannounced Penetration Test may have variants or specific types depending on the particular needs or requirements of the organization. These variations could include agreements tailored for specific sectors like finance, healthcare, or government entities. Additionally, there might be agreements that cover different testing scenarios, such as black-box, gray-box, or white-box penetration testing approaches. These approaches differ in the amount of information provided to the ethical hacker about the systems and networks under examination. In conclusion, the Delaware Ethical Hacking Agreement for External Network Security — Unannounced Penetration Test is a crucial document that sets the foundation for a secure and productive penetration testing engagement. It ensures that ethical hacking is conducted within legal and ethical boundaries, providing organizations with valuable insights into their external network's security posture and helping them enhance their overall cybersecurity defenses.
Delaware Ethical Hacking Agreement for External Network Security — Unannounced Penetration Test is a comprehensive and vital document that outlines the terms and conditions for conducting ethical hacking activities on an organization's external network. This agreement ensures that both parties involved, the organization and the ethical hacker, are aware of their responsibilities, rights, and limitations during the penetration testing process. The primary aim of the Delaware Ethical Hacking Agreement for External Network Security — Unannounced Penetration Test is to assess the robustness and vulnerabilities of an organization's external network by simulating real-world cyberattacks without prior notice. This type of penetration test aims to evaluate the effectiveness of the existing security measures and identify potential weaknesses that malicious actors could exploit. This agreement covers various aspects to provide a clear framework for the penetration testing engagement. It defines the scope of the test, including the specific systems, networks, and applications that will be targeted. It also specifies the testing techniques and tools that will be used, adhering to industry best practices and ethical guidelines. Moreover, the Delaware Ethical Hacking Agreement for External Network Security — Unannounced Penetration Test states the timeframes and schedules agreed upon for the testing process to minimize disruption to the organization's operations. It also establishes the rules of engagement, such as what actions the ethical hacker can perform and what should be avoided to prevent any damage or unauthorized access. This agreement also addresses the legal aspects, emphasizing that the ethical hacker should not engage in any illegal activities during the testing process. It ensures that all applicable laws and regulations are respected, and the ethical hacker acts within the boundaries of authorized activities. The Delaware Ethical Hacking Agreement for External Network Security — Unannounced Penetration Test may have variants or specific types depending on the particular needs or requirements of the organization. These variations could include agreements tailored for specific sectors like finance, healthcare, or government entities. Additionally, there might be agreements that cover different testing scenarios, such as black-box, gray-box, or white-box penetration testing approaches. These approaches differ in the amount of information provided to the ethical hacker about the systems and networks under examination. In conclusion, the Delaware Ethical Hacking Agreement for External Network Security — Unannounced Penetration Test is a crucial document that sets the foundation for a secure and productive penetration testing engagement. It ensures that ethical hacking is conducted within legal and ethical boundaries, providing organizations with valuable insights into their external network's security posture and helping them enhance their overall cybersecurity defenses.