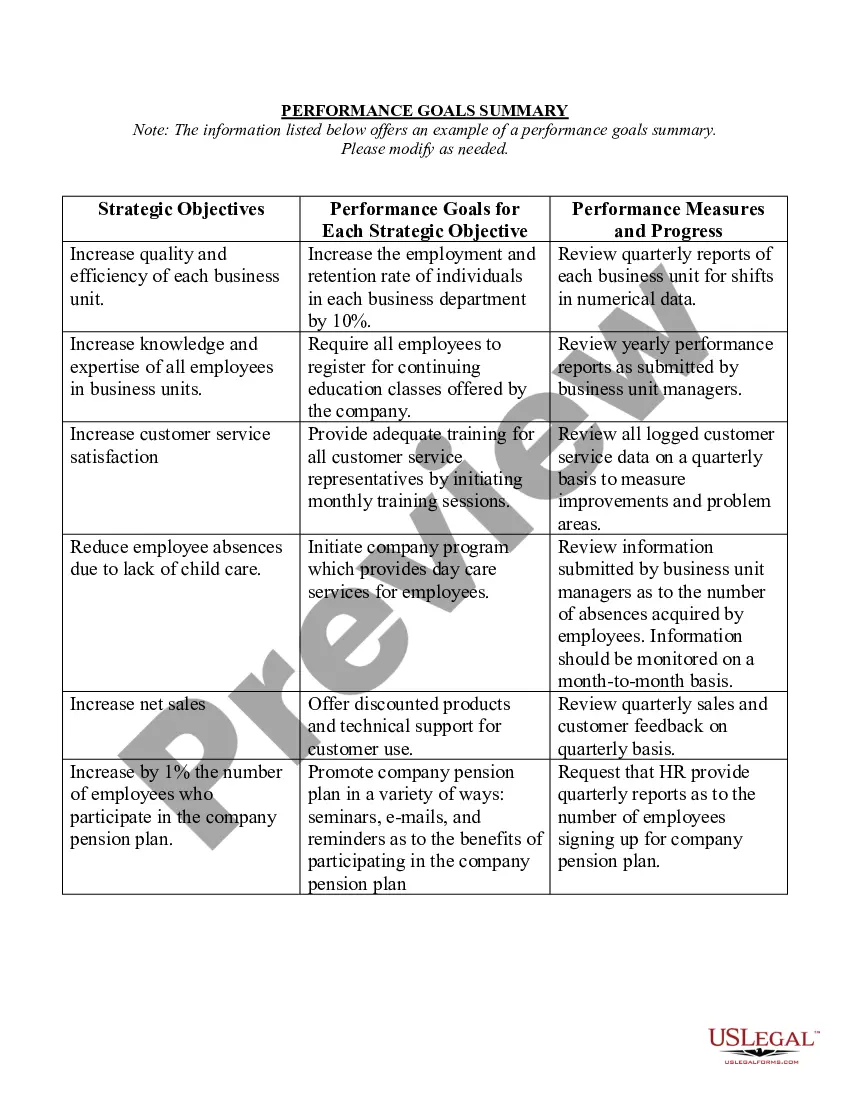
Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers
Description
How to fill out Detailed And Specific Policy With Regard To Use Of Company Computers?
You have the ability to spend hours online searching for the authentic document template that meets the local and federal regulations you require.
US Legal Forms offers thousands of legitimate documents that are assessed by experts.
You can easily download or print the Pennsylvania Detailed and Specific Policy Regarding Use of Company Computers from our platform.
If you want to find another version of the document, use the Search field to locate the template that fits your needs and requirements.
- If you already possess a US Legal Forms account, you may Log In and select the Download option.
- Subsequently, you can complete, modify, print, or sign the Pennsylvania Detailed and Specific Policy Regarding Use of Company Computers.
- Every legal document template you obtain is yours permanently.
- To acquire another copy of the downloaded form, navigate to the My documents section and click the corresponding option.
- If you are using the US Legal Forms site for the first time, follow the simple instructions below.
- First, ensure that you have selected the correct document template for your region/area of choice. Review the form description to verify you have chosen the right document.
- If available, use the Review option to look through the document template as well.
Form popularity
FAQ
Acceptable use of computers refers to the behavior and actions considered appropriate when using company devices and networks. This concept encompasses guidelines that prevent misuse, enhance security, and promote productivity. A Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers provides a clear framework for employees, outlining acceptable practices and ensuring that everyone is on the same page regarding computer usage.
The GDPR acceptable use policy establishes guidelines for the handling of personal data within organizations operating in the European Union. It stresses the necessity of respect for users' privacy and the protection of their information. Implementing a Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers can support GDPR compliance, as it sets clear expectations for treating personal data responsibly within your organization.
The ISO 27001 acceptable use policy is part of an information security management system aimed at protecting sensitive data. This standard emphasizes the importance of proper computer usage to mitigate risks associated with unauthorized access. A Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers can enhance your security framework by integrating ISO 27001 principles, ensuring a robust approach to data protection.
An acceptable ICT use policy outlines the appropriate usage of computer resources in an organization. This policy helps ensure that employees understand their responsibilities and the potential consequences of misuse. Within the framework of a Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers, such a document guides users on proper conduct, maintaining security, and protecting company assets.
Usage restrictions are defined by an Acceptable Use Policy (AUP), which delineates the behaviors expected of employees when using company systems. By clarifying what constitutes responsible use, this policy aligns with the Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers. It provides a clear framework that promotes security and integrity within the organization.
An acceptable use policy for a company computer is a formal agreement that outlines the appropriate ways employees can use company technology. This policy emphasizes the importance of responsible computing practices, such as avoiding prohibited websites and protecting sensitive data. The Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers serves as a foundation for creating a safe and secure workplace.
An Acceptable Use Policy (AUP) is a specific type of policy that outlines how a computer network or system can be used. This policy plays a crucial role in enforcing guidelines for users, shaping their interactions with company technology. It's integral to the Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers, ensuring all employees understand their responsibilities.
The Group Policy Results tool is effective for determining the applicable policy settings for a computer or user account if IT transitions to a different container. By analyzing the settings, organizations can ensure compliance with the Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers. This tool assists in identifying any necessary adjustments to maintain security and usability.
The process of steganography utilizes one message to conceal another. This technique ensures that sensitive information remains protected from unauthorized access. In the context of the Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers, employing such encryption methods enhances data security and compliance across the organization.
The Pennsylvania Detailed and Specific Policy with Regard to Use of Company Computers outlines the rules governing computer usage within an organization. This policy establishes expectations for employees on acceptable use, privacy, and security standards. Adhering to this policy helps maintain a professional work environment and protects company assets.