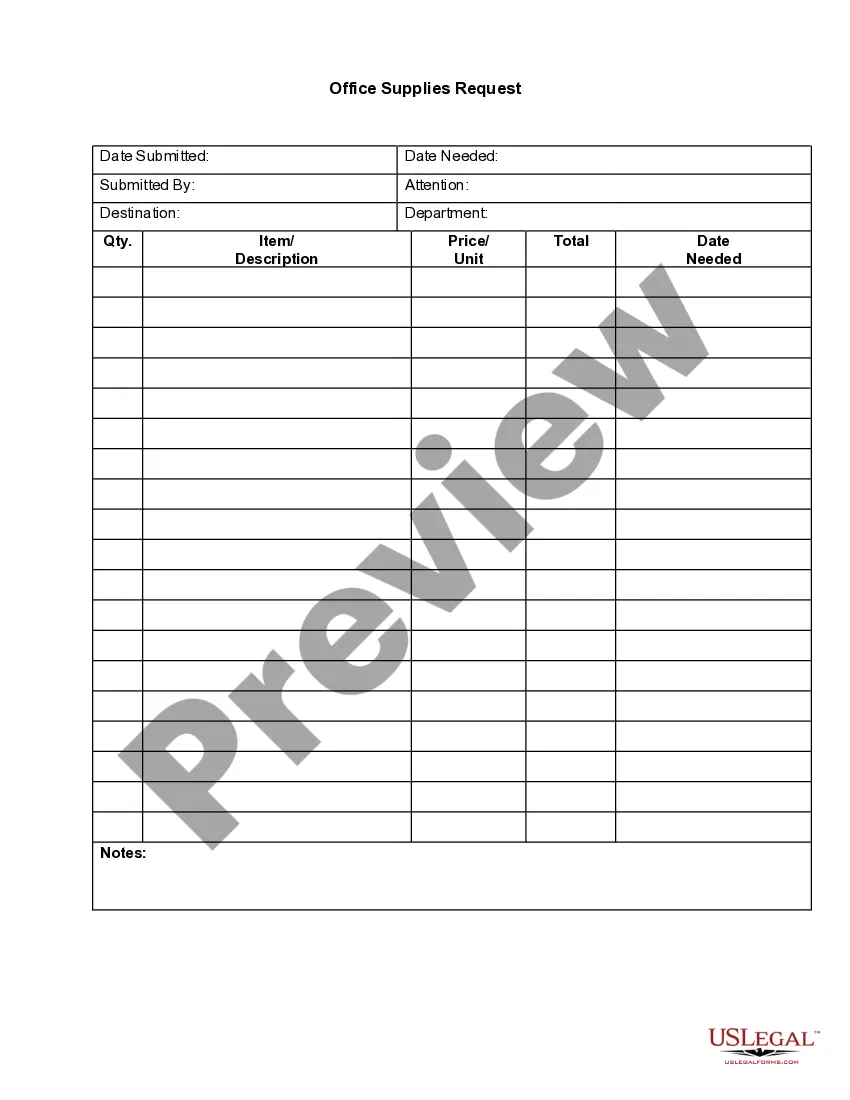
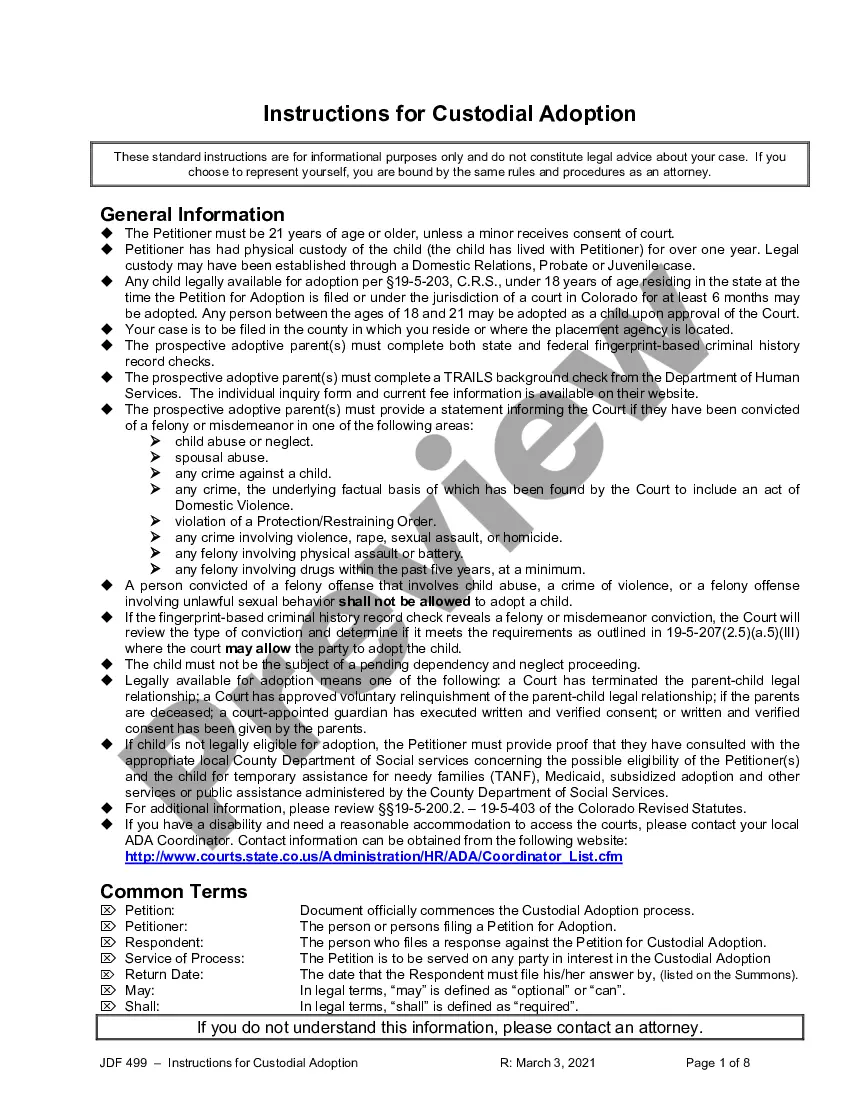
4.10 Direct Threat Defense is a type of security measure that is designed to protect computer systems from malicious attacks. It employs a set of techniques and technologies to detect, identify, and prevent malicious activity. These techniques include access control, application control, network protection, intrusion detection and prevention, data protection, and endpoint protection. Different types of 4.10 Direct Threat Defense include: • Access Control: This technique is used to restrict the access to computer systems. It involves setting up authorization and authentication mechanisms to grant users access to only those resources that they need in order to perform their tasks. • Application Control: This is a form of application-level security that is used to control the execution of applications and prevent malicious code from executing. • Network Protection: This technique is used to protect networks from malicious traffic by implementing firewalls, intrusion detection systems, and other network security measures. • Intrusion Detection and Prevention: This technique is used to detect and respond to malicious activity on a network. It involves monitoring network traffic for suspicious activity and blocking any malicious traffic. • Data Protection: This is a form of data security that is used to protect sensitive data from unauthorized access. It involves encrypting data and using other measures to ensure that it is secure. • Endpoint Protection: This is a form of endpoint security that is used to protect endpoints from malicious activity. It involves deploying anti-virus and anti-malware software and using other measures to protect endpoints.
4.10 Direct Threat Defense is a type of security measure that is designed to protect computer systems from malicious attacks. It employs a set of techniques and technologies to detect, identify, and prevent malicious activity. These techniques include access control, application control, network protection, intrusion detection and prevention, data protection, and endpoint protection. Different types of 4.10 Direct Threat Defense include: • Access Control: This technique is used to restrict the access to computer systems. It involves setting up authorization and authentication mechanisms to grant users access to only those resources that they need in order to perform their tasks. • Application Control: This is a form of application-level security that is used to control the execution of applications and prevent malicious code from executing. • Network Protection: This technique is used to protect networks from malicious traffic by implementing firewalls, intrusion detection systems, and other network security measures. • Intrusion Detection and Prevention: This technique is used to detect and respond to malicious activity on a network. It involves monitoring network traffic for suspicious activity and blocking any malicious traffic. • Data Protection: This is a form of data security that is used to protect sensitive data from unauthorized access. It involves encrypting data and using other measures to ensure that it is secure. • Endpoint Protection: This is a form of endpoint security that is used to protect endpoints from malicious activity. It involves deploying anti-virus and anti-malware software and using other measures to protect endpoints.